The Truth About Hacking In Five Minutes

Facebook, YouTube, Wikipedia, Amazon, Twitter, Instagram – all of these and even more web services, have become an integral and important part of our daily usage. Although these platforms are quite simple and easy to use, they all run a risk of being hacked. No one is insured against it or completely safe from this malicious intrusion.
However, what people can and must do to prevent such a possibility, is to understand and identify an obvious cyber threat towards their private data. Thus, the following questions arise: what exactly are the common methods used to exploit personal information, what is the reason behind it and most importantly, how to protect yourself against personal-based cyber-attacks?
Before answering any of the questions above, first let’s define what is hacking. Hacking is a process of an unauthorized intrusion inside a personal computer or organization network. A person who is not only using tools designed for hacking action, but understands the concept behind them and uses it to construct his own program, can be referred to as a hacker.
There are two characteristics of a hacker that have to be taken into attention and that is: determination and diligence. Both of these terms show on how focused and concentrated the person is, when he is performing an illegal act of hacking.
The general reason to why people turn to hacking is to steal and misuse information. Some of the common ways the information is misused are identity theft, bank money transaction, spamming, data leakage, blackmailing, etc. Just by knowing some of your major credentials details, such as bank account number, your full name and DOB, a hacker may be able to do a lot of damage.
Here are 3 common cyber attacks that occur to the regular users on the outer Web, along with the advice on how to identify them.
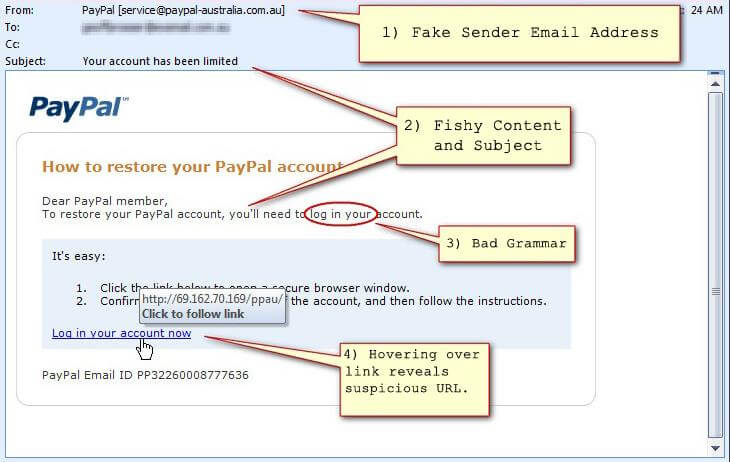
1) Fake phishing email from the “customer service”, with the malicious URL link.
Phishing – the act of sending the email to the targeted user, in order to create a false sense of authority and scam a person into giving his private data for identity theft. It is not only considered as a technical attack, but also a psychological one. The sense of urgency, authority, anger or any other feeling that can trouble the user and surrender his data to the attacker is a vital part of this attack.
The typical signs of such emails are:
• contain pictures or logos taken from the legitimate company website
• sender email address is close to a legitimate company, but slightly different from the official one.
• email will contain a link that will try to direct you to what you thought was the official website, but will actually direct you to a page where you enter your credentials
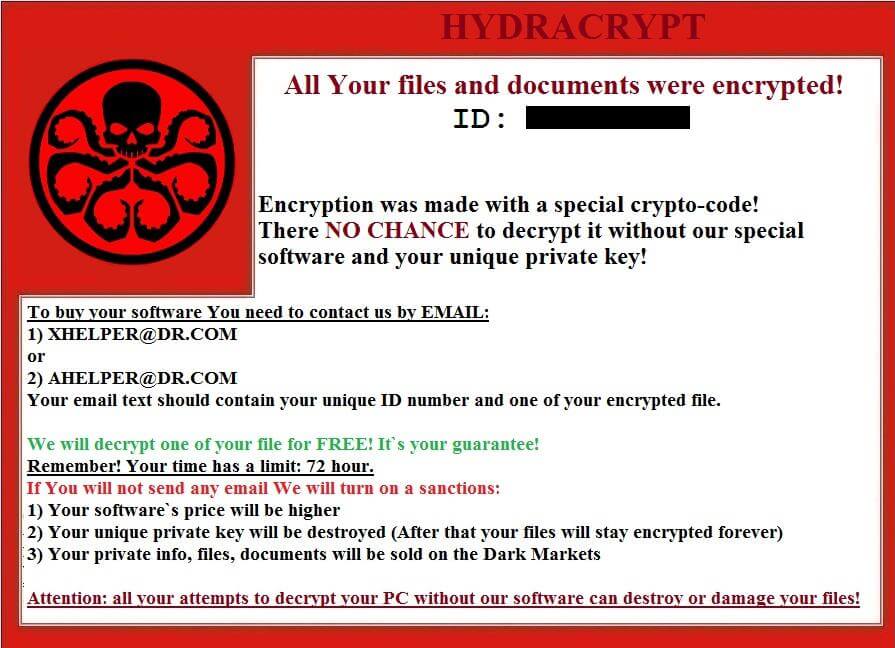
2) Hydracrypt – a type of Malware
Malware is commonly known as a general term for malicious software that may be a Virus, Trojan, spyware or adware. Once they are installed on your PC, these kind of software can seriously affect your system security and person’s private data, as it will secretly relay your confidential information to the third parties.
Such malicious programmes may hide within other software that the user is trying to install. Users might not know that they have accidentally installed such malware. After the installation of such files, a user may experience a sudden drop in a system overall performance, advertisement windows appearing in the operating system and constant crashes on the internet browser. It is advisable, that before installing any unknown software, a user must have a good antivirus and malware detector installed.
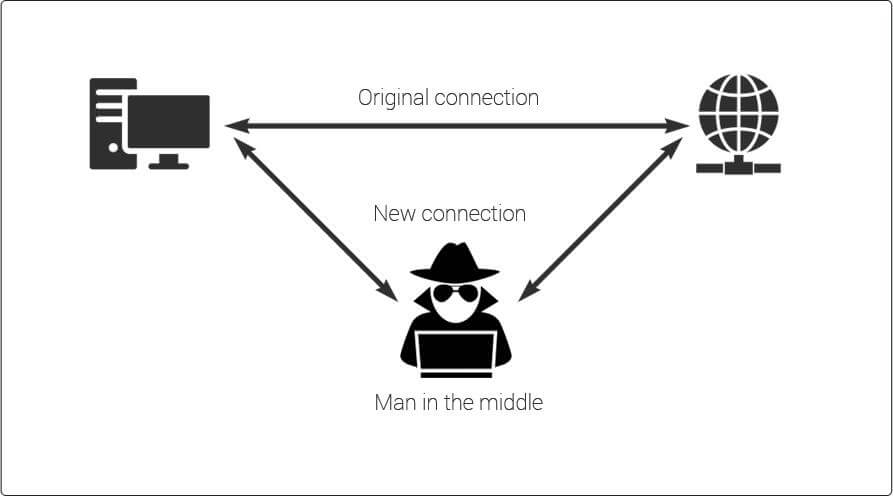
3) Man in the Middle – Interception of the communication medium by a 3rd party
Man in the Middle (MITM) is a type of a cyber-attack where the communication between two systems is being either intercepted or monitored by another entity. Such silent eavesdropping may occur on any type of communication channel: email, online messaging, and web surfing by hijacking personal email or the browser session.
Whenever, such attack is undergoing, it is very hard to check whether any third party is involved in the middle of the communication medium. However, a very obvious and noticeable fact about MITM is the time delay within the transmission channel.
Despite being a very dangerous attack, it doesn’t really mean that a user cannot completely avoid it. For example, Multipurpose Internet Mail Extensions or MIME for short, allows user to encrypt the sending email, so that only receiving end can read it. Another instance would be to provide correct TLS or SSL certificates on the websites, by utilizing HTTPS protocol in your browser.
With continued advancement of Information Technologies, it will be vulnerable to hacking no matter how complex the systems are. What folks like me and you can do is to be aware of the existence of such cyber threats, keep the security of their systems up to date in order to reduce possible windows for cyber attacks or hacking.